
When the pandemic forced a rapid swap to remote work, collaboration technologies were rolled out almost overnight. This immediate response to the need for effective collaboration tools was impressively fast, and essential at the time. However, the expeditated nature of rolling out these solutions meant some of them were put into place without robust governance and security policies, meaning many are now struggling to govern and secure these platforms effectively.
With this in mind, we decided to take stock of our customer’s M365 instances a few years post deployment. With a lens on ROI, we examined the common challenges they were facing and what they could do in terms of optimisation, governance, enhancements, and security.
Here’s some common challenges we found and solutions to help you mitigate risk and unnecessary expenses.
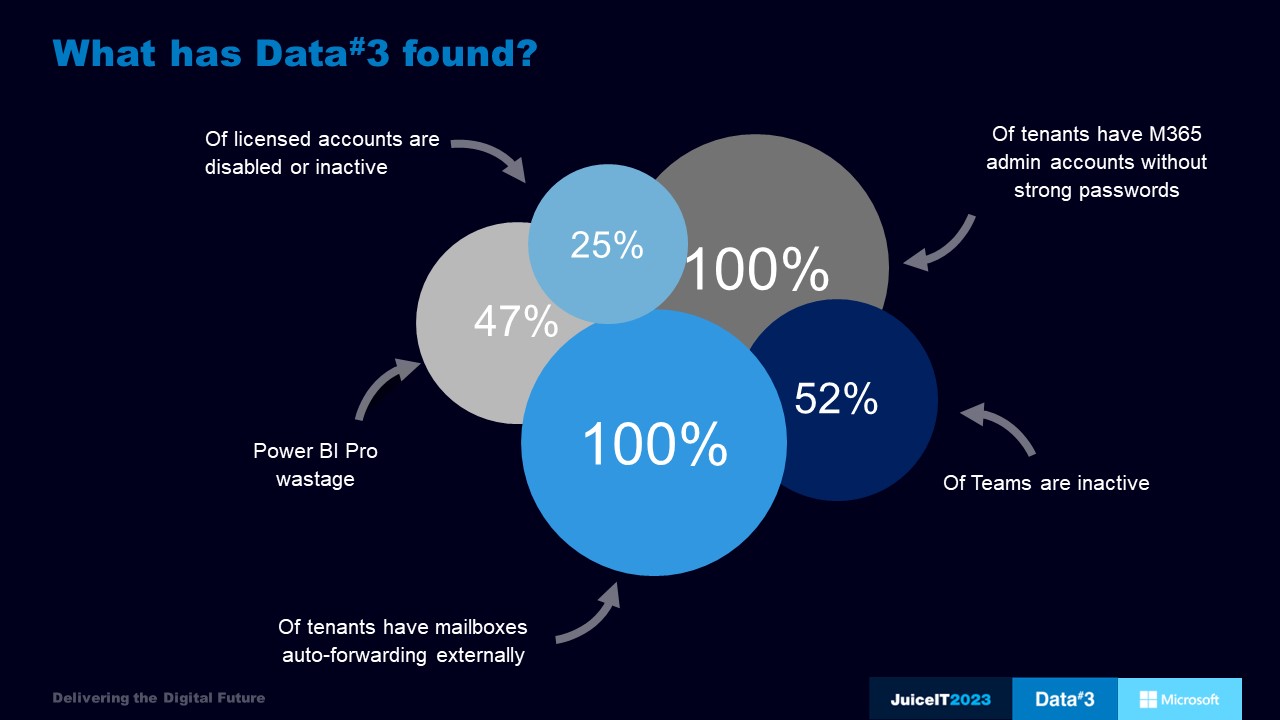
Summary of key findings
Let’s begin with wastage – on average, 25% of M365 licenses have become inactive.
Another common issue is security. Of all the tenants examined, every single one had some admin accounts that didn’t require strong passwords by default. All tenants have some mailboxes auto-forwarding emails externally. In 95% of these cases, it came down to the end user setting up the rules in Outlook. This highlights the need for security gaps to be addressed through policy and education, not left to individuals.
With the accelerated take up of Microsoft 365 in the past few years, issues like the above are all too common. As the business grows, staff come and go. If there is no governance, and no one keeping a watchful eye, cost and productivity spirals.
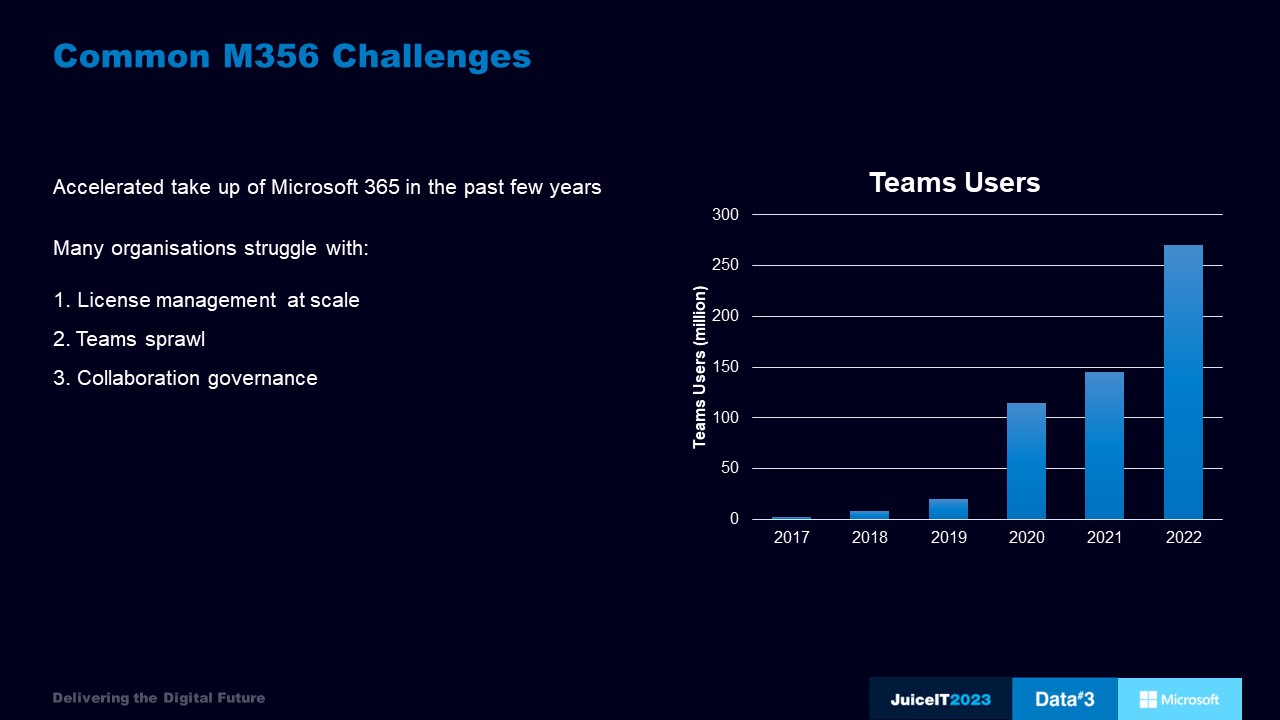
To tackle the challenge of license management at scale you can leverage data and third-party solutions or services such as Data#3’s M365 Optimiser. This will help boost adoption rates and cut down on licensing expenses, including:
Automating comprehensive user lifecycle management also helps cost savings through activities such as re-harvesting inactive licenses, stepping down licenses for staff on extended leave, and automatically deallocating licenses during the offboarding process.
To address Teams sprawl, we recommend locking down who can create new Teams to avoid clogging up the system. However, if you solely rely on IT to create a new Team the process can take too long, and collaboration will not be as effective. The answer lies somewhere in between – for example, a new Teams approval process could be implemented. Keep in mind that Teams become ownerless when a user leaves so it’s essential to identify inactive teams and either archive or assign a new owner.
Collaboration governance refers to securing data by limiting how things are shared.
For SharePoint, you can balance productivity benefits, such as external collaboration, while still securing your data. You can do so by disabling guest access to SharePoint sites with sensitive information and turning off anonymous links.
For OneDrive, you can use the OneDrive Retention settings to amend data retention times. The default is 30 days, and the max is 3,650 days. Additionally, OneDrive Sync settings should be configured to allow only domain-joined or hybrid-joined workstations to sync files to reduce data leakage.
For Teams, Group Naming policies can also be configured in AAD to ensure consistency. Consider using Sensitivity Labels to allow users to choose the sensitivity of the Team and apply appropriate security or retention policies.
Communication should be the same experience no matter where staff are located, and the M365 environment offers features that enhance hybrid work. For example, it’s worth noting that many Teams Phone System licenses are being paid for but are not in use. Which means capabilities like cloud voicemail, caller ID, call park, call forwarding, auto attendants, call queues, call transfer, and caller ID remain untapped.
Looking to the very near future, Teams Premium is set to bring AI into the meeting experience by integrating with GPT. This will provide AI-generated notes, tasks, and chapters.
In addition, the low-code Microsoft Power Platform is another technology worth exploring. A great example of its potential is the ability to extend an old, on-prem line-of-business app to the cloud. By harnessing these technologies, the work environment can become even more efficient and productive.
We don’t need to tell you that challenges around securing the modern workplace are complex and ever-increasing. Firewalls secured everything around 20 years ago, but today with the cloud, that protection isn’t cutting it. The Australian Government (2022) Notifiable Data Breaches Report tell us that in the first half of 2022, there were almost 400 notifiable breaches, with 41% of them being cyber-attacks. Most of these attacks were through phishing or compromised identity.
Combined with the absolute explosion of data, it’s clear that if you aren’t already worried about information protection and governance – you should be! Because your stakeholders are.
But there’s good news. If you’re familiar with Microsoft’s Security Incident and Event Management (SIEM) tools, you will be happy to hear that all that data can be consolidated and correlated using Microsoft Sentinel and Microsoft 365 Defender.
Most cyber-attacks start with a phishing email, as it’s an easy way for an attacker to gain initial foothold into the target organisation. Once the attacker has established initial access, they take advantage of a security flaw within an operating system or application.
This is where the M365 Defender security stack comes into play, with Defender for Endpoint quickly detecting and responding to advanced attacks. Microsoft Defender for Identity identifies advanced threats, monitoring and analysing user behaviour and activities to quickly discover reconnaissance attempts, the use of compromised credentials, and lateral movement paths.
In addition, Azure AD Identity Protection watches for any attempts to brute force accounts and monitors the dark web for stolen credentials. Defender for Cloud Apps provides further protection by detecting and preventing data exfiltration through the use of information protection policies via API integration.
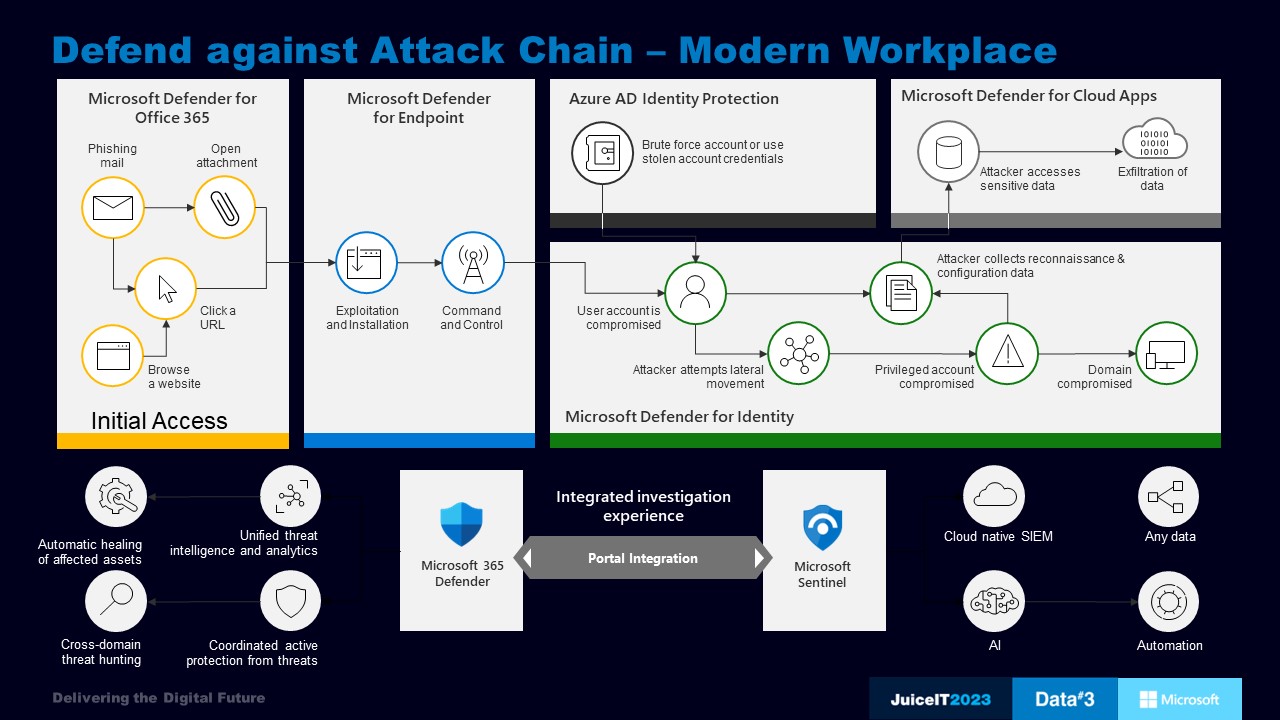
Microsoft 365 Defender and Microsoft Sentinel are closely integrated, allowing SecOps to start the investigation in Microsoft Sentinel where they have access to all data across the entire organisation. This allows them to pivot into Microsoft 365 Defender when they need deeper insight into incidents related to their Microsoft 365 environment.
For a much deeper look into how you can confidently secure your workplace with Microsoft, take a look at another newly released blog following the ‘Information protection in an age of information theft’ session at JuiceIT 2023.
The modern workplace is more complex than ever, and threats are ever-increasing. When everything comes together in an integrated investigation experience, organisations have the tools they need to protect users from cyberattacks and data breaches, without the management and cost burdens of more conventional approaches.
Data#3’s full-spectrum cybersecurity services and in-depth expertise with M365 will enable you to safeguard your organisation. Connect with our security team today to find out more.
Pandemic related technology rollouts in the height of the work from home movement shouldn’t be a burden. There are effective ways in which they can be reviewed, optimised, governed, and secured, for maximum efficiency, productivity, and increased ROI.
With more apps, devices, and data than ever to navigate, you need a business partner to guide and support you throughout your IT modernisation journey. Data#3 holds the highest level of partner accreditations across the Microsoft ecosystem. With expertise that extends from the network and the cloud, to the datacentre and workplace, you can rely on our expert team to guide and advise on the best technologies to meet the demands of the changing workplace.
Overcoming license wastage, security concerns and governance challenges starts here!
Information provided within this form will be handled in accordance with our privacy statement.