
Many tools and templates are available to help develop a cyber incident response plan (CIRP). In this blog, we’ll outline a simplified approach to CIRP planning and explore how advanced extended detection and response (XDR) solutions can streamline your CIRP.
An organisation’s ability to respond appropriately to a cyber security incident is a critical capability that must be developed, maintained, and refined – you can’t just rely on your security infrastructure to do the job. Much like business continuity and disaster recovery, handling a critical incident requires a carefully considered plan. This plan should ensure the right actions are taken, along with the associated people, processes, and technology capabilities to support that plan. Incident response planning is an essential governance and process control within any cyber security framework. However, according to an ASIC Spotlight on Cyber Report, 33% of organisations still don’t have a CIRP despite the significant focus on cybersecurity in the media, and at an executive level.
An effective approach to developing a CIRP should draw on principles from industry standards such as ISACA, NIST, ISO27001/27002 and the Australian Government Cyber Security Operations Guidelines. It’s important to remember that the plan is an evolving document – not set and forget – and just one part of a best practice-aligned security operations environment. We’ve included best practices for incident response planning a little later in this blog.
In the first blog of this series, we discussed the challenges of breach detection and the XDR tools improving detection rates. The effectiveness of any XDR tool directly impacts your CIRP – i.e., if your XDR tool can accurately detect and respond to a breach, your CIRP should consider these initial steps to avoid unnecessary escalations. Built-in capabilities can also simplify CIRP development.
Using Cisco’s XDR solution as an example, incidents promoted from security events are listed and ranked based on a priority score calculated from:
This ensures the most critical detections are surfaced at the top of the list, allowing your team to focus on what matters most.

You can then drill down further into the incident detail and view an attack graph that displays a compacted relationship view of the events causing the incident, and the targeted devices, entities, and resources. Having this information easily accessible allows for a clear decision-making framework to be developed in your CIRP, outlining when to escalate further and when the incident has been contained and/or eradicated.
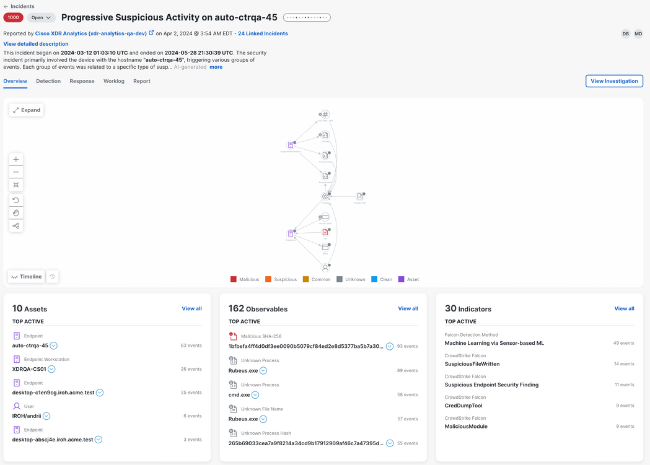
If further response action is required, Cisco XDR can manage your CIRP via playbooks that guide teams through incident response to effectively identify, contain, and eradicate the threat, and restore systems to recover from the threat.
These playbooks include tasks for all phases of incident response and the ability to document findings throughout the process. Some tasks also include workflows to automate parts of the response, and playbooks can be customised depending on the type of threat, e.g., ransomware vs data breach vs phishing. They can also be customised if needed according to your own CIRP, with the tasks and assignment rules developed for your organisation.

If we take a step back from the product-level capabilities of XDR, what should a best practice-aligned security operations environment look like? Many organisations define capabilities across five service areas – as per the European Union Agency for Cybersecurity (ENISA) whitepaper on CSIRT and SOC good practice:

Source: ENISA Good Practice Guide: How to set up CSIRT and SOC
Aligning your organisational program, accountabilities, and processes with these standards provides a robust framework for addressing security response capabilities while ensuring alignment with an organisation’s cyber security strategy.
At Business Aspect and Data#3, when we advise customers on developing or refining a CIRP, we break the planning process down into three broad phases which are adapted to our client’s environment and context while integrating and aligning with your existing organisational risk framework, processes, policies, and subsequent recovery processes. The plan should also integrate with existing processes including crisis management, disaster recovery, data restoration, business continuity, and key communications plans.

The CIRP typically includes:
The CIRP should also integrate with any detection methods associated with security operations processes and escalation paths. Good practice involves developing pragmatic incident response strategies that align with your organisation’s capabilities and culture. Notably, a key component of any CIRP is effective and appropriate communication both within and outside the organisation.
Finally, while it is important to have plans in place, it is equally important to test them thoroughly to validate the supporting policies and procedures and ensure system operability. Organisations should implement a CIRP testing strategy that includes key members of the response process, including core team members, organisational stakeholders, and external partners where appropriate.
Without a CIRP, you risk making mistakes during incident response that can exacerbate the unfolding crisis. Even if you have a CIRP, how much could your response capabilities be improved by adopting XDR?
Whether starting from scratch or needing to review and refine an existing CIRP to include XDR, it can be hard to know where to start.
That’s where existing templates can help – but solutions like Cisco XDR can also simplify the incident response planning process by providing a series of default actions and processes to follow that are already embedded in the tool responsible for detecting threats. It’s important to note that this approach won’t build you a comprehensive, overarching CIRP, but it does provide an easier, low-level starting point for developing it. More importantly, it gives you something concrete to work with quickly, while you take the time to add additional details and customise the plan to meet your organisation’s specific requirements.
Data#3 has one of Australia’s most mature and highly accredited security teams. Working in partnership with Cisco, we have been helping our customers achieve a more connected and secure organisation for more than 25 years. We can assist you in building your CIRP to test and refine existing response plans or with advice on simplifying and strengthening your security environment.
To learn more about these services and Data#3’s approach to incident response planning, contact us today for a consultation or to discuss a free trial of Cisco XDR.
