
Managing and safeguarding data across various apps, clouds, and endpoints is an uphill battle. It’s led to organisations relying on an assortment of tools to secure information which increase licensing costs, add management overhead, and expand the attack surface.
This brings us to the topic of this blog – Microsoft Purview Information Protection. This new unified suite of products works in conjunction to provide visualisation of sensitive data, data lifecycle protection, and data loss prevention. We’ll discuss the information protection challenges you’re likely facing, share a review of the capabilities offered by Microsoft Purview, and outline how to implement this solution across your hybrid environments – supported by Data#3 and Business Aspect.
Microsoft Purview – a significant revamp of the Azure Purview data-governance platform – is a collection of products that essentially work together to protect your data. The comprehensive solution includes a suite of compliance tools allowing you to view all your data assets in one place. They help you better protect, govern, and track the lifecycles of all your documents and data.
As you will soon learn, it’s got all the critical features needed to pave a smooth path to information security. These features include AI, automation, identity and access management, threat protection, cloud security, endpoint management, and privacy management capabilities – all under the one umbrella.
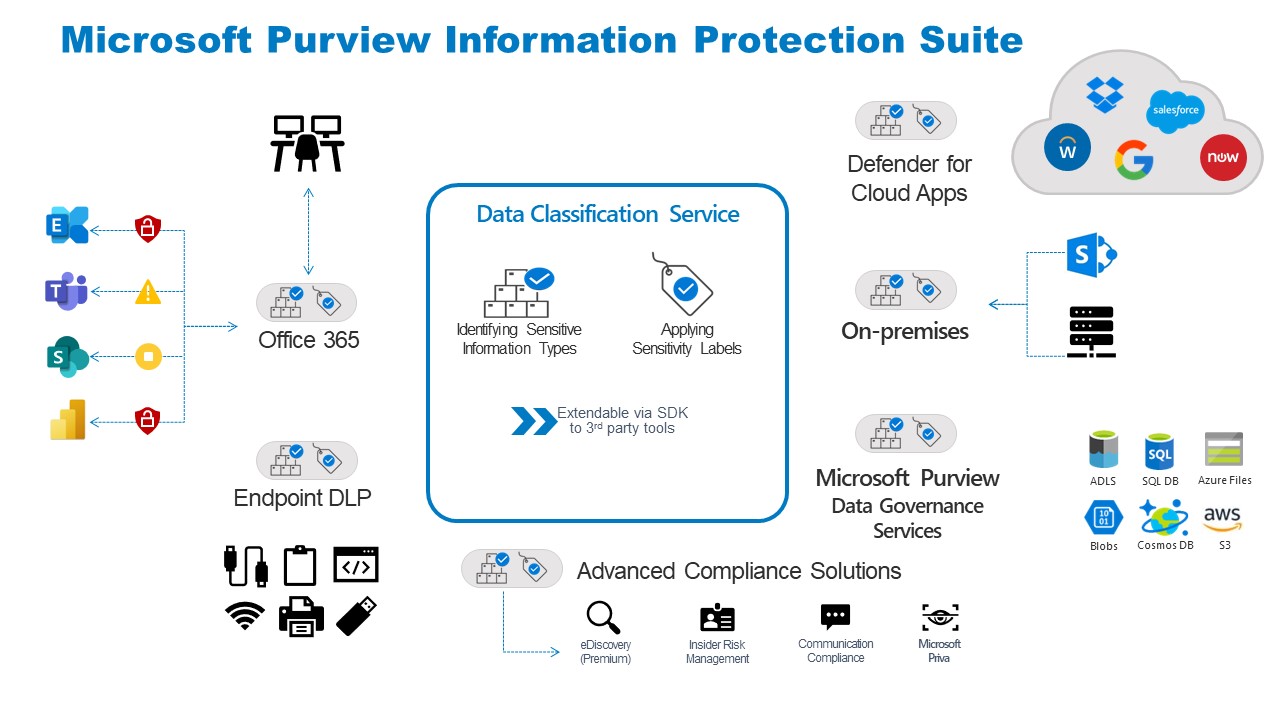
That’s the short story – let’s explore how it works.
Information protection is a security practice built on four pillars.
Microsoft Purview products incorporate these four pillars to provide well-rounded data protection across your entire environment. Here’s how it works.
Microsoft Purview allows you to classify data – automatically or manually – based on out of the box data types. By labelling data, you can treat data in specific ways and apply different policies at scale. This includes structured data such as credit card details, Privately Identifiable Information (PII), unstructured data such as employee ID numbers, invoice numbers, and quotation sequences.
Sensitivity labels can also be applied manually by users from other apps, such as Office 365 and SharePoint, or automatically, based on the detection of sensitive data in the document. These labels are portable and stitched into the metadata of the file, allowing them to follow the data into different environments where policies will be enforced.
Let’s use a real-case example to demonstrate how you can set Microsoft Purview up for success. We’ll use Data#3’s methodology as the example to show we live and breathe what we suggest customers put in place.
Microsoft Purview is not just a technical implementation. It’s a business implementation as well. Working together, the teams at Data#3 and Business Aspect combine expertise to provide a strategic and technology-infused solution.
Our methodology focuses on the following:
Now let’s dive into the information protection framework, highlight the outcomes that will assist your organisation, and share our learnings from many implementations.
Our implementation framework consists of five steps:
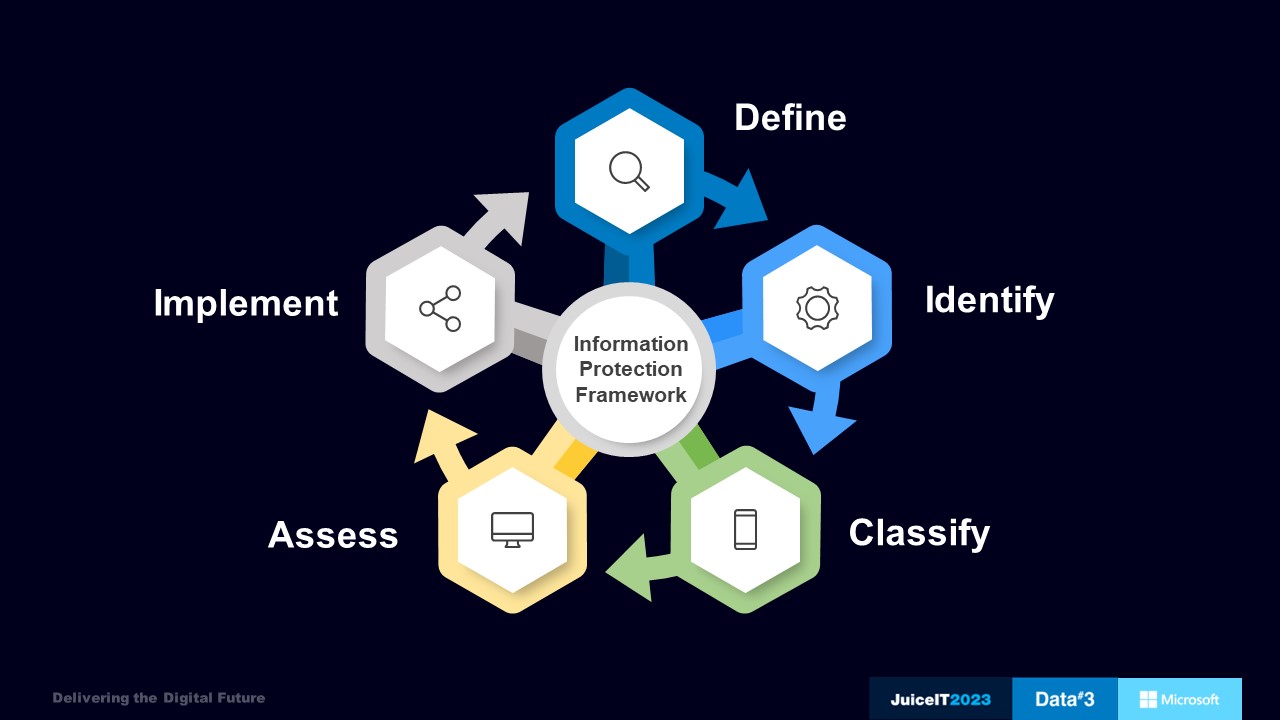
To classify data, the classification framework must be documented, with business rules and requirements clearly understood. Business buy-in to governance frameworks is critical, and the data scope (data location, type, and disposition) must be understood.
Outcomes:
To identify the touchpoints where data is stored, business processes must be examined, and assessments made at a high level. An initial data scan, and tools like Purview Scanner, can track down all sensitive data points.
Outcomes:
Building an initial information register is where the rubber really hits the road and starts to deliver value. This is when we engage with business leaders to identify data and work through the classification of that data. This is particularly vital, given that over or under-classifying data can lead to a breach in customer data.
The completed asset register will become a living document cataloguing all data and systems, including the type of information, repositories, access information, and business unit ownership. It’s crucial to review classifications regularly and validate assumptions about data, ensuring appropriate levels of protection. This process also presents an excellent opportunity to ditch old or irrelevant files.
Outcomes:
During the assess phase, we evaluate the existing controls over their information assets in line with the Information Handling Guidelines. This is when we review current controls in place to safeguard information, including access restrictions, encryption, process limitations, and guidelines for use. It’s crucial to identify any gaps or conflicts between the existing controls and the developed framework.
Through this assessment, it’s common to find that some controls are already in place but not implemented across the organisation. Additionally, process-oriented controls may exist instead of technical controls, which can lead to enforcement issues. However, it’s important to note that most of the time, people are trying to do the right thing, and any risks or issues are usually due to technological limitations, not malice.
Outcomes:
This is when we implement additional control requirements, such as configuration changes, to existing technical solutions, or further technical controls and associated processes. It’s essential to determine the approach for implementation and avoid using a big bang approach that may not be appropriate due to organisational change. The control implementation should be scoped into future detection, monitor, and prevention phases, including trainable classifiers and organisational regex.
The goal is to detect risks early on. Monitoring can assist with organisational change, training, and tuning of rules. Finalising operational support and day-to-day management is also addressed. We’ve learned that organisations should avoid biting off more than they can chew and take an agile approach across controls and business units. Some parts of the business may adopt faster and easier than others, and business process change may be required.
Outcomes:
Finally, as with all security solutions, this is not a set and forget solution. Regular reviews are required to monitor the environment. You need to check the effectiveness of the controls put in place, see if any new risks have emerged, and keep policies and procedures up to date.
Data protection is a critical element for any organisation. As organisations grow and store more data, it’s incredibly important to manage and protect that data. Microsoft Information Protection Suite is a powerful suite that, when paired with the technical and business expertise of Data#3 and Business Aspect, will ensure your data is protected effectively.
Every organisation creates masses of data – documents, presentations, emails and more – much of which can become stale or unused, and potentially pose privacy and regulatory risks. To address this issue, our Protect & Govern Sensitive Data Workshop includes a data risk check, utilising Microsoft Purview tools and services to automatically discover and analyse data stored in the Microsoft Cloud for any potential risks. It’ll show you how to:
View other complimentary Microsoft Security and Modern Workplace Workshops to find one that suits your needs.
me>