
This isn’t another “what is zero-trust” article – I think we can all agree that we’ve moved beyond that as we know it isn’t a product, it’s not a replacement for firewalls or VPNs, and it’s not something you do and then move on.
However, it is essential and appears in some form on virtually every government department’s cybersecurity strategic plan. Some departments and agencies have made progress and implemented elements of the zero-trust model within their environment, but not at a broad enough level to provide the promised levels of protection. Hence, despite the plan, they’re still vulnerable to a cyber-attack.
If zero trust is essential and part of a plan, why are government departments and agencies struggling to implement it? This post will explore that question.
The imperative to adopt zero-trust security has never been clearer for government departments and agencies. In an era of remote work, cloud-based services, and increasingly sophisticated cyber threats, zero-trust is an additional, identity-based layer that reduces the reliance on increasingly ineffective perimeter defences.
Driven by mandates from federal, state, and local authorities (such as the new Cyber Security Bill 2024), and the recognition that a new security model is needed, government entities are eager to embrace the principles – but reality on the ground tells a different story. Despite the strategic importance of zero trust, many government entities are struggling to turn that vision into tangible action for a number of reasons.
As a result, many government organisations find themselves stuck in a paradoxical situation. They know zero trust is where we all need to be, but the path remains elusive. Instead of bold action, their security roadmaps remain tactical and address the next pressing need rather than being a strategic, long-term plan that is continuously checked and aligned to.
In a recent discussion with a financial industry CISO, they revealed that these pitfalls are all too common. Despite an acknowledgement of the need for zero trust in their cybersecurity plan, and a multi-million dollar investment, they also:
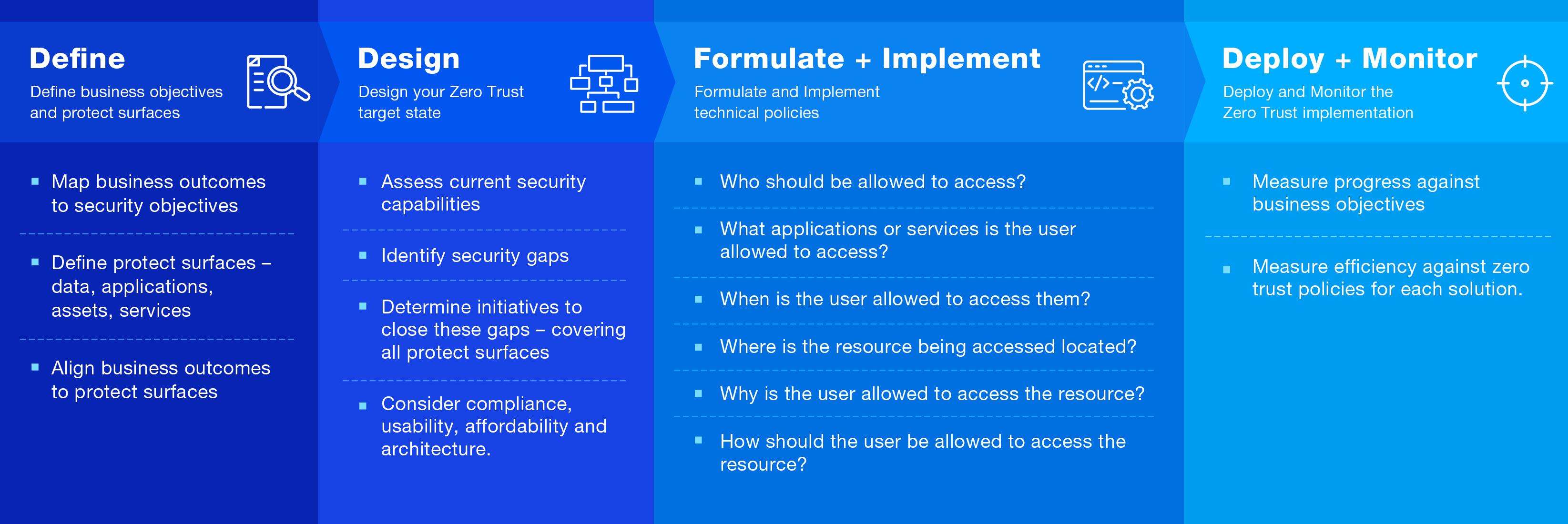
Breaking free of this paradox requires a fundamental shift in mindset and approach. Rather than viewing zero trust as a product- or tool-based, all-or-nothing proposition, government agencies must embrace a more strategic, process-driven incremental path forward. They can chart a course towards zero trust success by focusing on their most critical assets, prioritising use cases, and partnering with experienced advisors who take this process-driven approach.
Without trivialising the difficulties of implementing zero trust, there are some principles to consider:
 Do this by conducting an audit to pinpoint the most sensitive data, applications, and systems requiring the highest level of protection. Then, identify your Protect Surface DAAS elements – Data, Applications, Assets, Services.
Do this by conducting an audit to pinpoint the most sensitive data, applications, and systems requiring the highest level of protection. Then, identify your Protect Surface DAAS elements – Data, Applications, Assets, Services.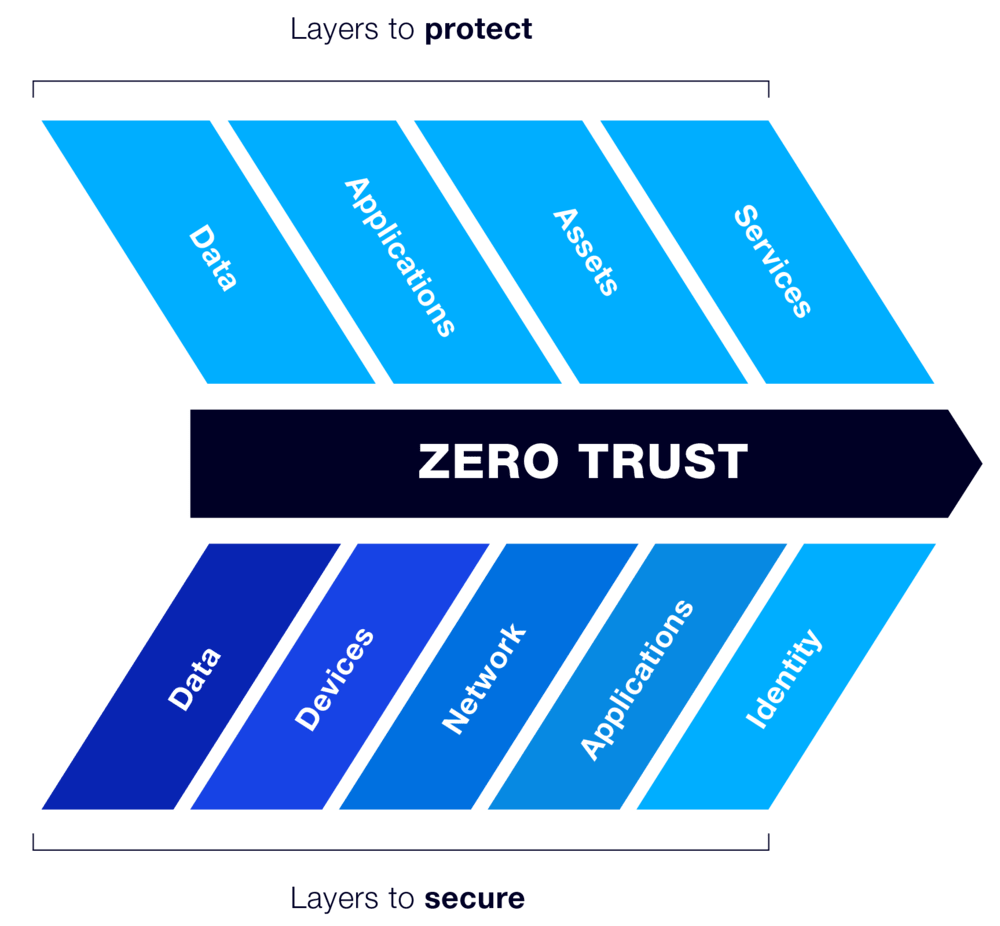
While tools and solutions are a component of the zero-trust model, they too often become the focus of government security teams looking for tangible ways to move forward. While tools can provide valuable data points, implementing zero trust effectively requires a more holistic, process-driven approach. Simply relying on a tool to assess one’s zero-trust posture is insufficient.
That’s why working with experienced advisors like Data#3 and Business Aspect, who can guide you through a comprehensive readiness assessment and the development of a practical zero-trust roadmap, is critical. This process-oriented approach, rather than a tool-centric one, can ensure that government entities have a clear understanding of their current state, their priorities, and the steps needed to achieve their zero trust goals.
This includes:
The final factor is understanding the vendor landscape. Vendor solutions are a critical implementation component, and aligning the right vendor solution is easier for a partner like Data#3, with its extensive vendor relationships and accreditations.
For example, government entities that have made significant investments in Cisco networking could use Data#3’s 25+ year relationship with Cisco to access their extensive security portfolio and zero-trust capabilities.
Implementing zero trust is a marathon, not a sprint. Government entities can chart a course toward a more secure, adaptable, and future-proof security architecture by taking a phased, strategic approach—identifying critical assets, assessing current capabilities, and partnering with experienced advisors. If you would like to discuss further please reach out to me using the contact button below or contact your account manager.

Data#3, in partnership with Cisco, will be hosting Security Resilience Assessment Workshops in 2025. These workshops will guide you through a self-assessment of your security posture using the updated CISA Zero Trust Model.
Register your details below to receive an invitation.